n00bzunit3d 2024 forensics/disk golf
Welcome to my series of writeups for n00bzunit3d 2024 capture-the-flag competition. In this post, we look at the forensics/disk golf challenge. The challenge gives us a .img file. These files are usually disk dump files. First thing we did was to open the file in Active@ Disk Editor to inspect the file contents. We did a search for the usual suspects n00bz, flag.txt and got lucky with the latter.
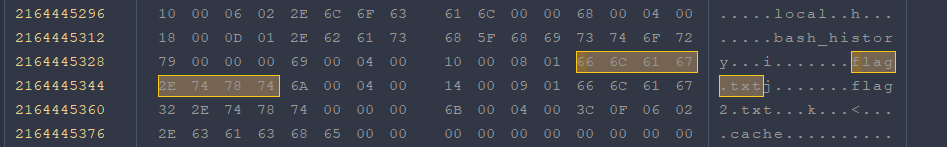
There seems to be a file called flag.txt present in the disk dump.
We turn to Autopsy which allows us to explore the file system in the img file.
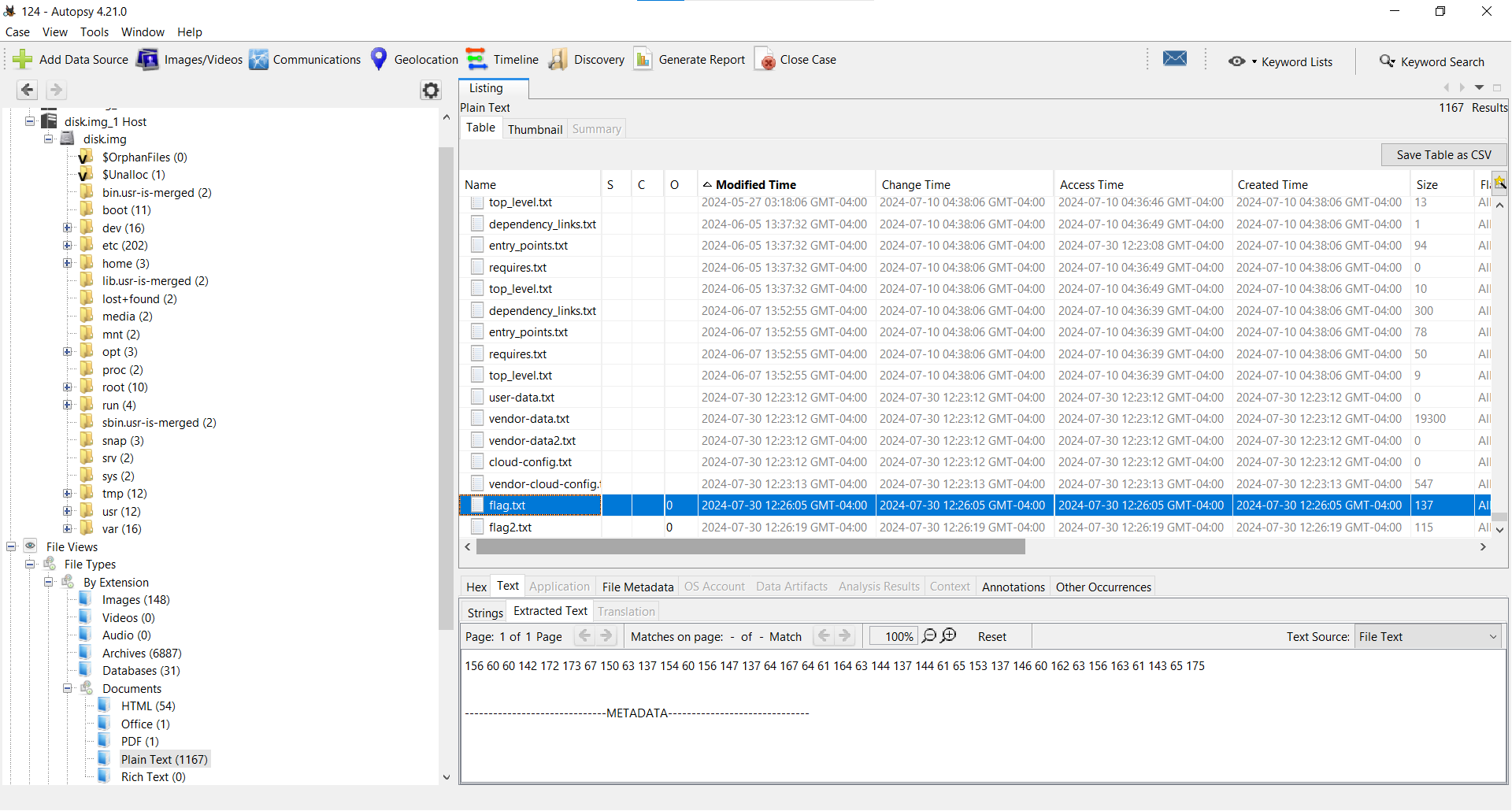
We filter by text documents and we find the flag.txt contains
156 60 60 142 172 173 67 150 63 137 154 60 156 147 137 64 167 64 61 164 63 144 137 144 61 65 153 137 146 60 162 63 156 163 61 143 65 175
These are obviously encodings of some kind. Converting to ASCII values yields no results. Next stop, hexadecimal to ascii - no luck. And now for the number system I honestly forget exists most the time - octal. Converting octal to ascii gives us the flag.
P.S: The flag2.txt file was for a challenge that was never released.